CMSmap是一个Python编写的针对开源CMS(内容管理系统)的安全扫描器,它可以自动检测当前国外最流行的CMS的安全漏洞。 CMSmap主要是在一个单一的工具集合了不同类型的CMS的常见的漏洞。CMSmap目前只支持WordPress,Joomla和Drupal。
主要功能
1.其可以检测目标网站的cms基本类型,CMSmap默认自带一个WordPress,Joomla和Drupal插件列表,所以其也可以检测目标网站的插件种类;
2.Cmsmap是一个多线程的扫描工具,默认线程数为5;
3.工具使用比较简单,命令行的默认的强制选项为target URL;
4.工具还集成了暴力破解模块;
5.CMSmap的核心是检测插件漏洞,其主要是通过查询数据库漏洞网站(www.exploit-db.com)提供了潜在的漏洞列表。
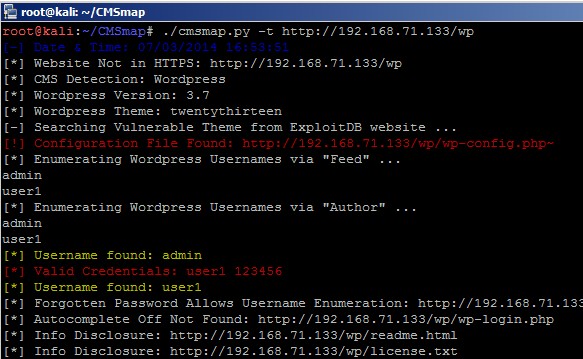
运行截图
暴力破解如下图:
Cmsmap检测到一个可以上传插件的用户的标示(可能是admin),cmsmap就会上传一个webshell。下图可能cmsmap的wp插件安装列表:
除了具有有效的凭证,在这访问webshell的攻击者能够执行操作系统命令,并试图进一步提权。
下载地址
https://github.com/dionach/CMSmap
写在最后
Cmsmap可以上传用户自定义的wenshell,CMSmap还支持WordPress的和Joomla密码哈希的离线暴力破解。牛逼的python大牛们,可以尝试,将我们国内的cms的漏洞写工具中。
[参考信息来源dionach.com,转载须注明来自FreeBuf黑客与极客(FreeBuf.COM)]
-
点赞…… 肯定是有大牛写过国内CMS的检测工具,只是木有共享出来而已…… 大牛们,放出来吧
不容错过
- 基于约束的SQL攻击鸢尾2017-01-06
- 互联网公司WAF系统设计chengfangang2017-03-08
- 苹果高管公开反对iPhone解锁提议,美国政府将与苹果公司对簿公堂FireFrank2016-03-11
- 逆向工程(三):实例破解VillanCh2015-12-02
0daybank




 关注我们 分享每日精选文章
关注我们 分享每日精选文章




已有 16 条评论
Kali Linux!
刚好需要wp得密码破解就来了
点赞…… 肯定是有大牛写过国内CMS的检测工具,只是木有共享出来而已…… 大牛们,放出来吧
这么好的工具,带有秘密破解功能。希望我可以用得好。
下载地址的超链有问题 不是https://github.com/dionach/CMSmap
404了连接
@ wa1t!ng 好好看看url:https://github.com/dionach/CMSmap 不要</code>
不支持win平台?
这个不错,漏洞精而全就好。
我咋用不了!
密码破解不能用嘞?
莫非不能批量?不是说可以用
5.CMSmap的核心是检测插件漏洞,其主要是通过查询数据库漏洞网站(www.exploit-db.com)提供了潜在的漏洞列表。
但是为什么木有全自动和批量呢?
转发微博
什么意思?发现的露洞,早都发补丁了,卖软件?还是反钓鱼?,,,,哦!有补不上的露洞是吧!!!!
root@macbook:/usr/share# git clone https://github.com/BrianHeeseIs/CMSmap.git
正克隆到 ‘CMSmap’…
remote: Counting objects: 451, done.
remote: Total 451 (delta 0), reused 0 (delta 0), pack-reused 451
Receiving objects: 100% (451/451), 43.00 MiB | 77 KiB/s, done.
Resolving deltas: 100% (279/279), done.
root@macbook:/usr/share# cd CMSmap/
root@macbook:/usr/share/CMSmap# ls
CHANGELOG.txt drupal_plugins.txt LICENSE.txt TODO.txt wp_timthumbs.txt
cmsmap.py drupal_versions.txt README.md wordlist wp_versions.txt
common_files.txt joomla_plugins.txt shell wp_plugins.txt
DISCLAIMER.txt joomla_versions.txt thirdparty wp_themes.txt
root@macbook:/usr/share/CMSmap# python cmsmap.py
CMSmap tool v0.3 – Simple CMS Scanner
Author: Mike Manzotti mike.manzotti@dionach.com
Usage: cmsmap.py -t <URL>
-t, –target target URL (e.g. ‘https://abc.test.com:8080/’)
-v, –verbose verbose mode (Default: false)
-T, –threads number of threads (Default: 5)
-u, –usr username or file
-p, –psw password or file
-o, –output save output in a file
-k, –crack password hashes file (WordPress and Joomla only)
-w, –wordlist wordlist file (Default: rockyou.txt)
-U, –update update CMSmap to the latest version
-h, –help show this help
-f, –force force scan (W)ordpress, (J)oomla or (D)rupal
Example: cmsmap.py -t https://example.com
cmsmap.py -t https://example.com -f W
cmsmap.py -t https://example.com -u admin -p passwords.txt
cmsmap.py -k hashes.txt
root@macbook:/usr/share/CMSmap# python cmsmap.py -t http://www.yatanarpon.net.mm/ -v -f D
[-] Date & Time: 13/05/2015 14:49:10
[*] Website Not in HTTPS: http://www.yatanarpon.net.mm/
[-] HTTP Header Protections Not Enforced …
X-XSS-Protection
Strict-Transport-Security
X-Content-Security-Policy
[*] Robots.txt Found: http://www.yatanarpon.net.mm//robots.txt
[-] Searching Vulnerable Theme from ExploitDB website …
Traceback (most recent call last):
File "cmsmap.py", line 1698, in <module>
scanner.ForceCMSType()
File "cmsmap.py", line 166, in ForceCMSType
DruScan(self.url,"default",self.threads).Drurun()
File "cmsmap.py", line 728, in Drurun
ExploitDBSearch(self.url, "Drupal", [self.Drutheme]).Themes()
File "cmsmap.py", line 969, in Themes
htmltext = urllib2.urlopen("http://www.exploit-db.com/search/?action=search&filter_description="+self.cmstype+"&filter_exploit_text="+theme).read()
TypeError: cannot concatenate ‘str’ and ‘NoneType’ objects
root@macbook:/usr/share/CMSmap# python cmsmap.py -v -f D -t http://www.monstate.gov.mm/
[-] Date & Time: 13/05/2015 14:50:09
[*] Website Not in HTTPS: http://www.monstate.gov.mm/
[-] HTTP Header Protections Not Enforced …
X-XSS-Protection
Strict-Transport-Security
X-Content-Security-Policy
[*] Robots.txt Found: http://www.monstate.gov.mm//robots.txt
[*] Drupal Version: 7.28
[-] Searching Core Vulnerabilities for version 7.26
[*] Vulnerable Core Version 7.26 Found: http://www.exploit-db.com/exploits/36996
[*] Vulnerable Core Version 7.26 Found: http://www.exploit-db.com/exploits/36978
[*] Vulnerable Core Version 7.26 Found: http://www.exploit-db.com/exploits/36979
[*] Vulnerable Core Version 7.26 Found: http://www.exploit-db.com/exploits/36980
[*] Vulnerable Core Version 7.26 Found: http://www.exploit-db.com/exploits/36981
[*] Vulnerable Core Version 7.26 Found: http://www.exploit-db.com/exploits/36982
[*] Vulnerable Core Version 7.26 Found: http://www.exploit-db.com/exploits/36984
[*] Vulnerable Core Version 7.26 Found: http://www.exploit-db.com/exploits/36986
[*] Vulnerable Core Version 7.26 Found: http://www.exploit-db.com/exploits/36987
[*] Vulnerable Core Version 7.26 Found: http://www.exploit-db.com/exploits/36988
[*] Vulnerable Core Version 7.26 Found: http://www.exploit-db.com/exploits/36989
[*] Vulnerable Core Version 7.26 Found: http://www.exploit-db.com/exploits/36990
[*] Vulnerable Core Version 7.26 Found: http://www.exploit-db.com/exploits/36991
[*] Vulnerable Core Version 7.26 Found: http://www.exploit-db.com/exploits/36992
[*] Vulnerable Core Version 7.26 Found: http://www.exploit-db.com/exploits/36993
[*] Vulnerable Core Version 7.26 Found: http://www.exploit-db.com/exploits/36949
[*] Vulnerable Core Version 7.26 Found: http://www.exploit-db.com/exploits/36950
[*] Vulnerable Core Version 7.26 Found: http://www.exploit-db.com/exploits/36951
[*] Vulnerable Core Version 7.26 Found: http://www.exploit-db.com/exploits/36953
[*] Vulnerable Core Version 7.26 Found: http://www.exploit-db.com/exploits/36954
[-] Searching Core Vulnerabilities for version 7.25
[*] Vulnerable Core Version 7.25 Found: http://www.exploit-db.com/exploits/36996
[*] Vulnerable Core Version 7.25 Found: http://www.exploit-db.com/exploits/36978
[*] Vulnerable Core Version 7.25 Found: http://www.exploit-db.com/exploits/36979
[*] Vulnerable Core Version 7.25 Found: http://www.exploit-db.com/exploits/36980
[*] Vulnerable Core Version 7.25 Found: http://www.exploit-db.com/exploits/36981
[*] Vulnerable Core Version 7.25 Found: http://www.exploit-db.com/exploits/36982
[*] Vulnerable Core Version 7.25 Found: http://www.exploit-db.com/exploits/36984
[*] Vulnerable Core Version 7.25 Found: http://www.exploit-db.com/exploits/36986
[*] Vulnerable Core Version 7.25 Found: http://www.exploit-db.com/exploits/36987
[*] Vulnerable Core Version 7.25 Found: http://www.exploit-db.com/exploits/36988
[*] Vulnerable Core Version 7.25 Found: http://www.exploit-db.com/exploits/36989
[*] Vulnerable Core Version 7.25 Found: http://www.exploit-db.com/exploits/36990
[*] Vulnerable Core Version 7.25 Found: http://www.exploit-db.com/exploits/36991
[*] Vulnerable Core Version 7.25 Found: http://www.exploit-db.com/exploits/36992
[*] Vulnerable Core Version 7.25 Found: http://www.exploit-db.com/exploits/36993
[*] Vulnerable Core Version 7.25 Found: http://www.exploit-db.com/exploits/36949
[*] Vulnerable Core Version 7.25 Found: http://www.exploit-db.com/exploits/36950
[*] Vulnerable Core Version 7.25 Found: http://www.exploit-db.com/exploits/36951
[*] Vulnerable Core Version 7.25 Found: http://www.exploit-db.com/exploits/36953
[*] Vulnerable Core Version 7.25 Found: http://www.exploit-db.com/exploits/36954
[-] Searching Core Vulnerabilities for version 7.24
[*] Vulnerable Core Version 7.24 Found: http://www.exploit-db.com/exploits/36996
[*] Vulnerable Core Version 7.24 Found: http://www.exploit-db.com/exploits/36978
[*] Vulnerable Core Version 7.24 Found: http://www.exploit-db.com/exploits/36979
[*] Vulnerable Core Version 7.24 Found: http://www.exploit-db.com/exploits/36980
[*] Vulnerable Core Version 7.24 Found: http://www.exploit-db.com/exploits/36981
[*] Vulnerable Core Version 7.24 Found: http://www.exploit-db.com/exploits/36982
[*] Vulnerable Core Version 7.24 Found: http://www.exploit-db.com/exploits/36984
[*] Vulnerable Core Version 7.24 Found: http://www.exploit-db.com/exploits/36986
[*] Vulnerable Core Version 7.24 Found: http://www.exploit-db.com/exploits/36987
[*] Vulnerable Core Version 7.24 Found: http://www.exploit-db.com/exploits/36988
[*] Vulnerable Core Version 7.24 Found: http://www.exploit-db.com/exploits/36989
[*] Vulnerable Core Version 7.24 Found: http://www.exploit-db.com/exploits/36990
[*] Vulnerable Core Version 7.24 Found: http://www.exploit-db.com/exploits/36991
[*] Vulnerable Core Version 7.24 Found: http://www.exploit-db.com/exploits/36992
[*] Vulnerable Core Version 7.24 Found: http://www.exploit-db.com/exploits/36993
[*] Vulnerable Core Version 7.24 Found: http://www.exploit-db.com/exploits/36949
[*] Vulnerable Core Version 7.24 Found: http://www.exploit-db.com/exploits/36950
[*] Vulnerable Core Version 7.24 Found: http://www.exploit-db.com/exploits/36951
[*] Vulnerable Core Version 7.24 Found: http://www.exploit-db.com/exploits/36953
[*] Vulnerable Core Version 7.24 Found: http://www.exploit-db.com/exploits/36954
[-] Searching Core Vulnerabilities for version 7.23
[*] Vulnerable Core Version 7.23 Found: http://www.exploit-db.com/exploits/36996
[*] Vulnerable Core Version 7.23 Found: http://www.exploit-db.com/exploits/36978
[*] Vulnerable Core Version 7.23 Found: http://www.exploit-db.com/exploits/36979
[*] Vulnerable Core Version 7.23 Found: http://www.exploit-db.com/exploits/36980
[*] Vulnerable Core Version 7.23 Found: http://www.exploit-db.com/exploits/36981
[*] Vulnerable Core Version 7.23 Found: http://www.exploit-db.com/exploits/36982
[*] Vulnerable Core Version 7.23 Found: http://www.exploit-db.com/exploits/36984
[*] Vulnerable Core Version 7.23 Found: http://www.exploit-db.com/exploits/36986
[-] No HTTP/HTTPS provided. Assuming HTTP…
[-] Date & Time: 25/01/2017 13:23:03
[-] Target: http://122.114.226.9:9001
[M] Website Not in HTTPS: http://122.114.226.9:9001
[I] Server: Apache/2.4.7 (Ubuntu)
[I] X-Powered-By: PHP/5.5.9-1ubuntu4.19
[L] X-Frame-Options: Not Enforced
[I] Strict-Transport-Security: Not Enforced
[I] X-Content-Security-Policy: Not Enforced
[I] X-Content-Type-Options: Not Enforced
[L] No Robots.txt Found
[I] CMS Detection: WordPress
[I] WordPress Version: 4.5.5
[I] WordPress Theme: twentysixteen
[-] Enumerating WordPress Usernames via "Feed" …
[-] Enumerating WordPress Usernames via "Author" …
[M] admin
[M] liming
Traceback (most recent call last):
File "cmsmap.py", line 2033, in <module>
scanner.ForceCMSType()
File "cmsmap.py", line 194, in ForceCMSType
WPScan(self.url,self.threads).WPrun()
File "cmsmap.py", line 357, in WPrun
bruter.WPXMLRPC_brute()
File "cmsmap.py", line 1274, in WPXMLRPC_brute
htmltext = opener.open(req).read()
File "/usr/lib/python2.7/urllib2.py", line 429, in open
response = self._open(req, data)
File "/usr/lib/python2.7/urllib2.py", line 452, in _open
‘unknown_open’, req)
File "/usr/lib/python2.7/urllib2.py", line 407, in _call_chain
result = func(*args)
File "/usr/lib/python2.7/urllib2.py", line 1266, in unknown_open
raise URLError(‘unknown url type: %s’ % type)
urllib2.URLError: <urlopen error unknown url type: 122.114.226.9>
请问,为何会这样???Orz